
Securing Weather Insights: A Vault-Encrypted Journey with Airflow
In the realm of data security, safeguarding sensitive information is paramount. This blog delves into a project that utilizes HashiCorp Vault to encrypt and decrypt transformed weather data. The pipeline, orchestrated by Apache Airflow, exemplifies a robust approach to data security, ensuring that valuable insights remain confidential and protected.
High-level architecture diagram:
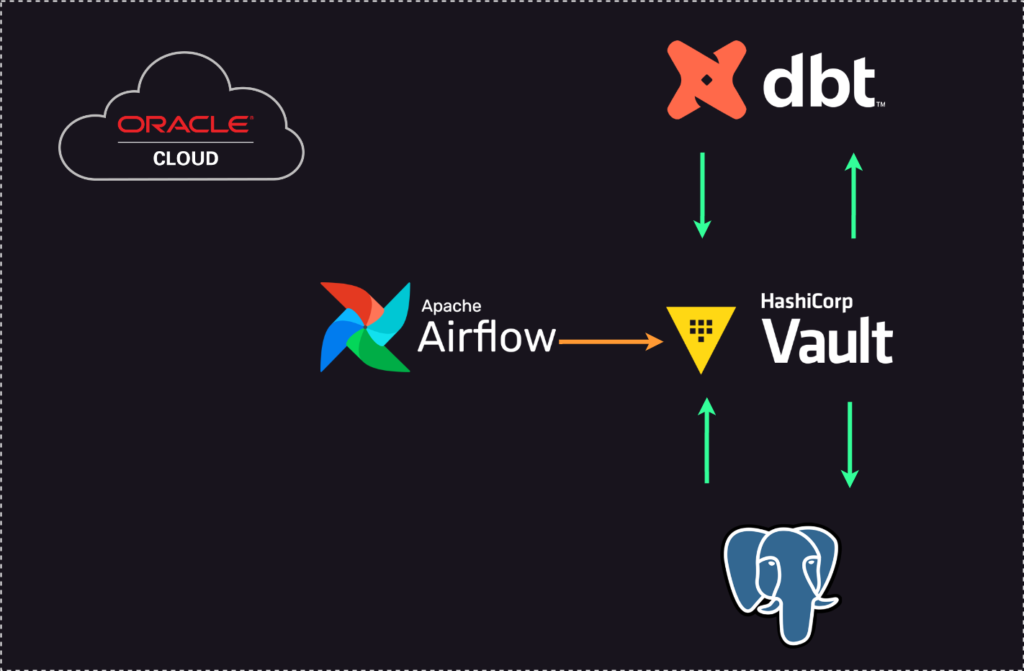
Phase 1: Transform and Encrypt with Vault
1.1 Data Transformation with DBT
Begin by leveraging DBT to transform the raw weather data into meaningful insights. The transformed data is then directed to a designated folder, weather_transformed.
1.2 Vault Encryption Layer
Introduce HashiCorp Vault to add an encryption layer to the transformed data. The data is encrypted and stored in a new folder, weather_transformed_vault. Vault ensures that sensitive information remains secure, adhering to best practices in data security.
Phase 2: Airflow Orchestration for Encryption and Decryption
2.1 Encrypting with Airflow DAG: “encrypt_and_store_data_to_postgres”
Create an Airflow DAG named “encrypt_and_store_data_to_postgres” to orchestrate the encryption process. This DAG triggers the execution of the DBT transformation and then directs the transformed data to be encrypted using Vault before storing it securely.
2.2 Decrypting with Airflow DAG: “decrypt_and_store_data_to_postgres”
Implement a corresponding Airflow DAG named “decrypt_and_store_data_to_postgres” for the decryption process. This DAG is responsible for retrieving the encrypted data from weather_transformed_vault, decrypting it through Vault, and subsequently storing it in Postgres.
Vault Encryption Workflow Overview
-
Data Transformation with DBT: Transform raw weather data into meaningful insights stored in
weather_transformed.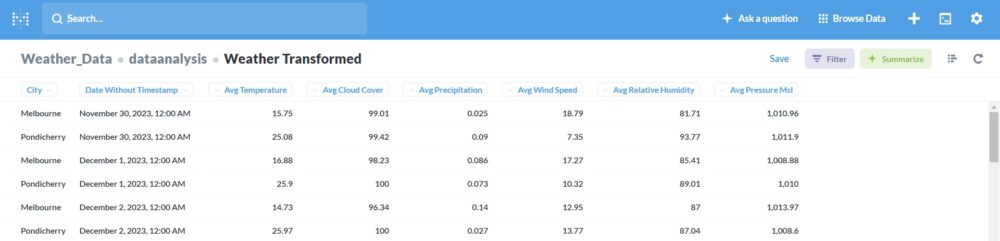
-
Encryption with Vault: Utilize HashiCorp Vault to encrypt the transformed data and store it in
weather_transformed_vault.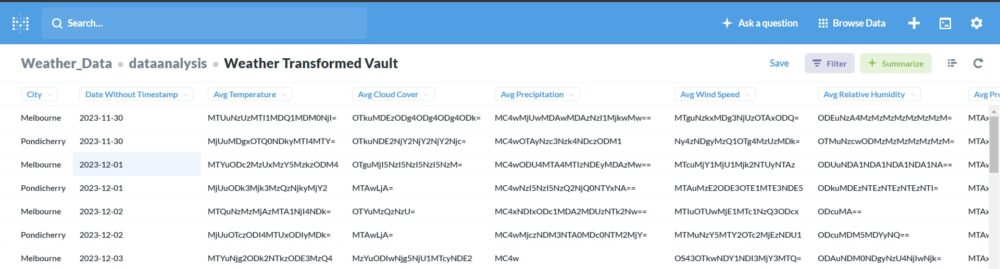
-
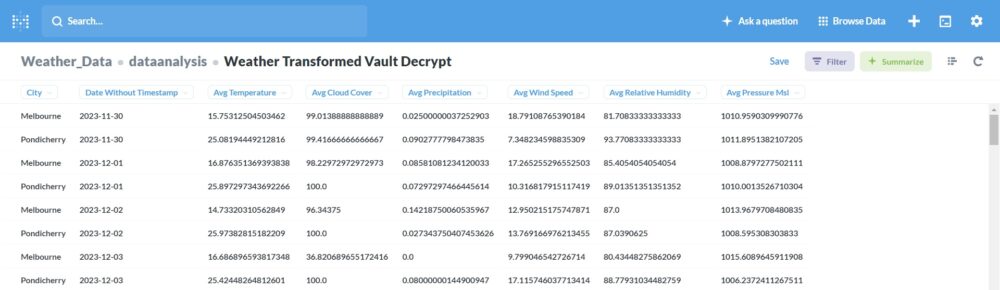
-
Airflow DAGs Orchestration:
- “encrypt_and_store_data_to_postgres”: Initiates the DBT transformation and encrypts the data using Vault before storing it securely.
- “decrypt_and_store_data_to_postgres”: Retrieves the encrypted data from
weather_transformed_vault, decrypts it through Vault, and stores it in Postgres.
Benefits of Vault Encryption in the Data Pipeline
-
Data Security: Vault ensures that sensitive information is encrypted, providing an additional layer of security.
-
Key Management: Centralized key management through Vault simplifies encryption key handling and rotation.
-
Compliance: Adherence to data security best practices ensures compliance with privacy regulations.
Conclusion: A Secure Data Journey
In conclusion, this project showcases the significance of incorporating encryption into your data pipeline using HashiCorp Vault. By integrating Vault with Airflow DAGs, the weather data undergoes a secure transformation and storage process. This not only safeguards sensitive information but also adheres to the highest standards of data security. As we continue to advance in the era of data-driven insights, ensuring the confidentiality and integrity of our data remains paramount. The orchestration capabilities of Airflow, combined with the security features of Vault, exemplify a robust and dependable approach to handling and protecting sensitive information.

